Last month, a Singaporean by the name of Mohammad Azhar bin Tahir was jailed for defacing the Prime Minister's official website. in 2013. This was in addition to the case of Delson Moo, who was fined SGD 8000 for a similar offense, this one concerning the Istana.
This is what happened to the PM's official website:
 |
| Screenshot 1 |
This is what happened to the Istana website:
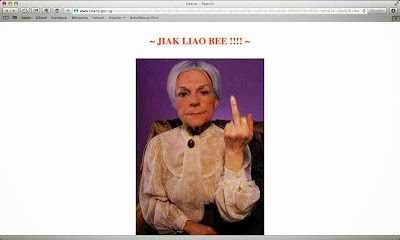 |
| Screenshot 2 |
The Singapore Police Force website was also defaced with an overlay of an image of two men
The Technical Specifics
The attacks were classified as a kind of Cross-Site Scripting (XSS) attack, where the attacker used the Search bar of the website to input codes that would overlay an image on top of the website, thus defacing it.More about XSS: http://en.wikipedia.org/wiki/Cross-site_scripting
Infocomm Development Authority of Singapore (IDA) claimed that the web sites were not hacked as both the Prime Minister's Office and Istana main sites were still working. Technically, they are correct - server data was not compromised and any damage done was on a superficial level. But it would be a mistake to say that the damage done was only on a superficial level. These were Government websites, and the Government (particularly those responsible for the website) was made to look like a bunch of rank amateurs. There is no "only" superficial damage.
Especially when you consider that the Prime Minister's official website was compromised not long after Prime Minister Lee Hsien Loong famously issued a warning to would-be attackers.
"It is not just anything goes and you are anonymous, therefore there is no responsibility. You may think you are anonymous. We will make that extra effort to find out who you are."
What did the attackers suffer? Some jail time, perhaps a fine of a few thousand bucks. And the government? A huge foot-in-mouth moment and a tremendous loss in credibility.
Yes, no data was lost, altered or stolen.
Yes, the damage was restricted to the visual aspect of the sites.
Yes, it could be worse. Way worse.
No, all this does not make it OK.
The average web-user is visual creature - he judges with his eyes. And since he can't see the database (which is intact) and can only see the front-end layout (which is not), he can hardly be blamed for assuming the worst. Loss of public confidence is not a small matter for those in authority.
But I'm glad these attacks were carried out. If nothing else, this has driven home a valuable point to the public, one which the average web developer would have known by now: Government websites are not extra-safe just because they are Government websites. In other words, don't trust the Government blindly, and don't place them on a pedestal. They're as fallible as the next man.
That's not to say I think that Government websites should be bulletproof. No site in the world is bulletproof - it is merely a matter of time and effort. What is appalling is that these websites could have been defaced using such a schoolboy method. All the attackers had to do was manipulate the search bar function, and in certain cases, just the URL. XSS Attacks come in countless forms - and the types of XSS attacks used to deface these websites were among the most unsophisticated.
Contrast this with what happened to the Swedish Government, also last month. Hackers broke into the email accounts of the Swedes. I'm sure I don't have to tell you that's a different class altogether from a crummy surface-level XSS attack.
A possible cause of the problem
To be fair though, it's not just these websites which have such vulnerabilities to exploit. Plenty of others do.In my time as a vendor-based developer, I've seen projects being outsourced to smaller companies, and even to outfits in India and Malaysia who would do the work for a fraction of the price quoted to the original customer. By the time the project went down the chain, what was originally a 10k project would likely have become a 1k project. These "factories" might churn out something resembling the specifications using off-the-shelf software. Visually the final product would be satisfactory, but what about security? Oh, you wanted your site to be watertight, too? Then maybe you should have paid for that, you cheap shit.
For those at the bottom rung of the outsourcing ladder, there are very few consequences for failure. I mean, can you see yourself suing some tiny firm in Timbuktu for botching a job you should have done yourself?
I didn't think so.
Stay vigilant. There's no such thing as XXS-ive security!
T___T
T___T
No comments:
Post a Comment